QuantumCare: your cybersecurity department and trusted consultant
A premium, always-on cybersecurity service for UK businesses with 10–250 staff. Instead of wondering if you’re “secure enough”, you get a dedicated partner acting as your in-house cyber department – monitoring, hardening and advising every day, without the full-time headcount.
UK‑based team • Clear monthly subscription • Cancel any time


QuantumCare Guide
QuantumCare is purpose-built for growing businesses that know cybersecurity isn’t optional — it’s critical.
QuantumCare is a premium cybersecurity protection service, capped at a maximum of 20 clients at any one time. It’s a great fit for organisations with 10–250 employees, £1M+ in annual turnover, and existing internal or outsourced IT support.
If you’re serious about protecting your business, your clients, and your reputation, QuantumCare gives you a dedicated cybersecurity partner that feels like part of your team. Prefer remote-first delivery, clear priorities, and ongoing expert guidance — not just a one-off fix? You’re exactly who we built this for.
Not sure if QuantumCare is the right fit for you? Click Schedule Consultation to talk it through — and don’t forget to check out our other cybersecurity services, which might be a more direct match for where you are today.
What makes up QuantumCare?
Always-on managed cybersecurity service
Firewalls
Blocking threats, backed up before changes
Switches & Wi-Fi
Kept healthy, updated and documented
Windows PCs
Patched, hardened and watched 24/7
Microsoft 365
Locked down with MFA, safer email and clean access
External Scans
See what attackers see
Staff Training
Annual training and phishing tests
Secure Disposal
Secure wiping when equipment is retired
The Real Business Outcomes
Transform cybersecurity from a cost center into a competitive advantage that drives growth and protects your bottom line
Maximize Productivity
Good cyber hygiene prevents IT disruptions
87%
Fewer IT issues through proactive security
- Security issues caught and fixed before they cause downtime
- Patched systems run faster and crash less
- Clean networks mean reliable connectivity
- Secure remote access that actually works
- Malware prevented = systems stay responsive
Reduce Total IT Costs
Prevent expensive emergencies with proactive protection
£45K
Average cost of breach prevented
- Avoid expensive emergency breach response costs
- Prevent ransomware payments and recovery expenses
- No data breach notification and legal fees
- Lower cyber insurance premiums with proven security
- Fixed monthly costs vs unpredictable crisis spending
Win More Business
Pass security audits and win enterprise contracts
Ready
For any security questionnaire
- Answer security questionnaires confidently
- Show documented security measures to prospects
- Meet supplier security requirements
- Demonstrate professional security standards
- Evidence your commitment to data protection
Protect Your Reputation
Build trust through visible security commitment
Trust
Your most valuable business asset
- No embarrassing breach notifications to clients
- Maintain customer confidence in your services
- Prove security commitment with certifications
- Stand out from less-secure competitors
- Build long-term client relationships on trust
Competitive Advantage
Turn security into your business differentiator
3x
More likely to win security-conscious clients
- Market your superior security standards
- Charge premium prices for secure services
- Enter new markets requiring compliance
- Partner with larger enterprises confidently
- Lead your industry in security practices
Peace of Mind
Sleep well knowing your business is protected
24/7
Expert protection and monitoring
- Know experts are watching your systems constantly
- Get clear updates in plain English
- Have a direct line to a security expert
- Reduce stress from security uncertainties
- Focus on growing your business, not protecting it
Within 30 days of QuantumCare, you'll be so well protected that cybercriminals will move on to easier targets—your less secure competitors.
The Framework We Use to Protect Your Company
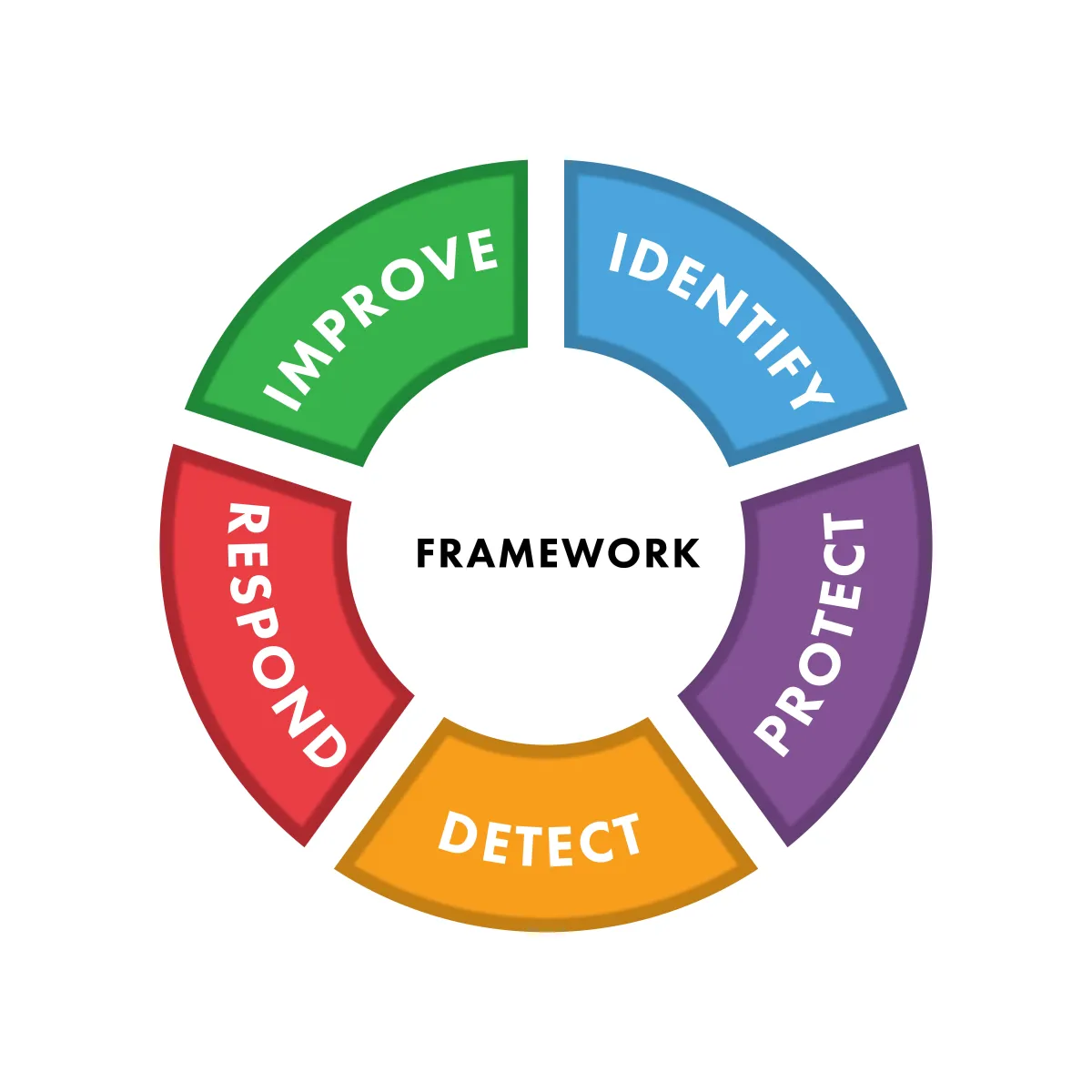
Lightning-Fast Response
With only 20 clients, we respond to your needs in minutes, not hours or days.
Dedicated Attention
Your business gets the focused protection it deserves from our expert team.
Personal Service
You'll know your security team by name, not ticket number.
Proactive Protection
We have time to hunt threats before they find you, not just react to problems.
Deeper Understanding
We learn your business inside out, spotting unusual activity others would miss.
Premium Resources
Enterprise-grade tools and expert time focused on fewer clients means better protection.
Secure Your Spot Today
Join an exclusive group of businesses that never worry about cybersecurity

Do we still need cyber insurance?
Yes. Think of QuantumCare as your daily protection and insurance as your financial back-up. We help you qualify and renew by providing the evidence insurers ask for, reduce your premium risk by tightening controls, and—if something happens—work with your insurer and legal team so claims go smoothly.
Do you guarantee we won’t ever be hacked?
No one credible can promise that. What we do guarantee is fast action and clear outcomes: quick detection, rapid containment, clean recovery tests, and a one-page board update each month. The goal is simple—fewer incidents, smaller impact, faster recovery—with proof you can show.
How is this different from our IT provider?
Your IT keeps the lights on. We focus on reducing business risk: watching for trouble, closing common gaps, and coordinating responses. We work with your IT, not instead of them.
What do you need from us to get started?
Three simple things—kept as light as possible:
- Install a small helper tool on each company device (you or your IT can do this; we’ll provide a click-by-click guide).
- Give us the right access to a few agreed areas so we can set things up and keep watch.
- Name a decision-maker we can reach quickly for approvals.
That’s it. We’ll handle the rest and keep you updated in plain English.
Is it all remote? What about on-site?
Most work is remote for speed and cost. If you need on-site help (e.g., a major incident or board session), we can arrange it—clearly scoped and scheduled.
Who is QuantumCare a good fit for?
UK organisations with 10–250 people who want predictable costs, clear reporting, and tangible improvements—not a one-off audit.
How will we know it’s working?
You’ll see simple monthly proof: how quickly we found issues, how fast we contained them, what improved, and what’s next. No long reports—just what leaders need.
Are we locked into a long-term contract?
No. QuantumCare is month-to-month. You can scale seats up or down and cancel with notice. For the finer points (notice period, minimum seats, what’s included), see our pricing page.

Innovation
Fresh, creative solutions.


Excellence
Top-notch services.

FOLLOW US
Systems Secure Ltd
6 The Meadow, Copthorne, West Sussex. RH10 3RG
07588 455611
Company Registration: 7295869
COMPANY
CUSTOMER CARE
LEGAL
Copyright 2026. Systems Secure. All Rights Reserved.
